Page 1 :
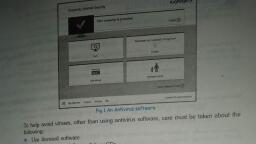
Onlike viruses and worms, spyware does not normally replicate itself. Bonzi Buddy, is an Do Tou KRow, example of a program bundled with spyware that is targeted at children. CoolWebSearch, Awure la w, Internet Optimizer(DyFuCa), Zango, HuntBar are all ezamples of spyjrate programs, Installing anti-spyware software on the computers is the best way to deal with it., that dieplaye, advertieing ban, on web hrowsers, wuch as Inter, Explorer, Mozilla, Malware, is derived from the words malicious and software, It is a software designed to creep Pirefox ete, Malware, Into or damage a computer system without the owner's knowledge or consent, This tern is, used to denote a variety of forms of interfering or troublesome software or program code., Remember, Malware includes computer vinusses, worms, trojan horses, spyware, fraudulerit adware and, other malicious and unwanted software., Some malware programs install a key logger, which then captures the user's keystrokes when, the user is entering a password. Data-stealing malware is a great threat to users. It robs the, victims of personal or confidential information like credit card numbers that may later on be, misused. Bancos, Gator, LegMir and Qhost are examples of data-stealing malware., E-mail spam, unwanted bulk, -mail, junk mail, or unweloome, commercial eme, •When a malice, attacker keeps, sending bulk maik, till the mail-serve, in full, it is knowS, as E-mail, Spam, Spam is the process of flooding the Interrniet with so many copies of the same message, in order, to force the message on people. Most spam is commercial advertising, often for questionable, products or services, get-rich-quick schemes etc,, bombing, E-mail spam is unwanted bulk e-mail, junk mail, or unwelcome commercial e-mail., Spamming is the practice of sending unwanted e-mail messages, frequently from an, unidentified source. Today spam comprises some 80 to 85% of all the e-mail in the world., When a malicious attacker keeps sending bulk mails till the mail-server is full, it is known as, E-mail bombing., Some other types of spam are:, Instant messaging spam, Newsgroup spam, Mobile phone spam, Online game messaging, spam and Blog and guestbook spam., 5.7 PROTECTING YOUR COMPUTER, Let us understand the basic requisites one must follow to protect the computer:, Do You Know?, Step 1. Use updated antivirus software, Viruses and spyware are two kinds of malicious software that you need to protect your the term spam is, computer from. You can prevent viruses, with the help of an antivirus program that is regularly derived from the, updated., It is widely believed, 1970 SPAM sketch of, Antivirus programs help the user to identify, neutralise or eliminate viruses. Such software the BBC television, typically takes the following actions :, comedy series Moty, Python's Flying, Circus'., * attempts to repair the file by removing the virus itself from the file, * quarantine the file (so that the file rermains inaccessible to other programs and its virus can, no longer spread), or, • delete the infected file if it was not possible to repair it, Computers-9, Cyber Sale, 86