Page 1 :
10, , Cyber Security and, Netiquette, , Learning Objectives, Understanding Cyber Security, , Understanding Netiquette, , Cyber Attacks, , Why do we need Netiquette?, , Common Types of Cyber Threats, , Principles of Proper Netiquette, , Cyber Safety Measures, , Introduction, The internet has become the integral part of today’s generation, of people, from communicating through instant messaging and, emails to banking, travelling, studying and shopping, internet, has touched every aspect of life. With the growing use of the, internet by people, protecting important information has become, a necessity., A computer that is not having appropriate security controls can be, infected with malicious software and thus any type of information, can be accessed in moments. Number of infected web pages and, malicious websites can be seen every day that infects the computer and allows hackers to, gain illegal access to other computer systems., , Understanding Cyber Security, In the digital world, security refers to the, precautionary steps taken to protect computing, resources against cybercrime. It is a technique of, protecting computers, networks, programs and data, from unauthorized access or attacks that are aimed, for exploitation., Cyber security is important because government, military, corporate, financial and medical, organizations collect, process and store unprecedented amounts of data on computers and, other devices., 148 Brainy Gigabyte+ 7
Page 2 :
A significant portion of that data can be sensitive information, whether it is intellectual, property, financial data, personal information or other types of data for which unauthorized, access or exposure could have negative consequences., , Definition, Cyber security refers to a set of techniques used to protect the integrity of networks, programs and data, from attack, damage or unauthorized access., , Cyber Attacks, The internet is a digital jungle and there are a wide range, of dangers waiting for you out there. Web-based threats, or online threats are malware programs that can target, you when you’re using the Internet. In simple words, a web, threat is any threat that uses the WWW (World Wide Web) to, facilitate cybercrime., A threat, in the context of computer security, refers to, anything that has the potential to cause serious harm to a computer system. It is something, that may or may not happen, but has the potential to cause serious damage. Threats can, lead to attacks on computer systems, networks and more., , Info, New Terms:, ‘Malware’: Short for ‘malicious software’, are refered to the computer programs designed to infiltrate, and damage computers without the users consent., Cyber Attack: It is an attempt to gain illegal access to a computer or computer system for the purpose, of causing damage or harm., , Common Types of Cyber Threats, Hacking, , Computers have become mandatory to run a successful business or an organization. It is, not enough to have isolated computer systems, they, need to be networked to facilitate communication with, external businesses or organizations. This exposes them, to the outside world and hacking. Hacking is the process, of gaining unauthorized access into a computer system or, group of computer systems or a website or a social media, site or an email account. This is done through cracking of, passwords and codes which gives access to the systems., Cyber Security and Netiquette 149
Page 3 :
The person who undertakes hacking is known as the hacker. They can access your computer, and private information directly, if you are not protected by security software. They can, monitor your conversations or missuse the back-end of your personal website., , Virus, , Just like human, can get viral infections, computer virus is a, threat for our computer system and cyber security too., Computer viruses are pieces of software that are, designed to be spread from one computer to another., Viruses are often attached to files for download, shared, via CD's, DVD's, or USB sticks. They’re often sent as email, attachments or downloaded from specific websites with, the intent to infect your computer and other computers, on your contact list by using systems on your network., Viruses are known to send e-mail spam, disable your, security settings, corrupt and steal data from your computer including personal information, such as passwords, even going as far as to delete everything on your hard drive., , Info, New Term:, Email spam, also known as junk email, is mass mailing over the internet by sending promotional messages, to practically everyone whose email address is known, without asking for anyone's permission., , Adware and Spyware, , Adware is a type of malware software that is designed to, track your browsing habits and based on that, show you, advertisements and pop-ups. The ads often redirect your, searches to advertising websites and collect marketingtype data about you, behind your back, which is considered, malicious. The presence of adware on your computer is, noticeable only in those pop-ups and sometimes it can slow, down your computer’s processor and internet connection, speed., Spyware works similar to adware, but is installed on your computer without your knowledge., Once installed on your computer, spyware can monitor your keystrokes, read and delete, your files, reformat your hard drive and access your applications. Whoever is controlling the, spyware has access to your personal information including email addresses, passwords, even, credit card numbers without you even knowing., 150 Brainy Gigabyte+ 7
Page 4 :
Phishing, , Phishing is method of social engineering with the goal of, obtaining sensitive data such as passwords, usernames, credit, card numbers etc., You receive an email that is made to look as though it comes, from a legitimate company(banker, insurance companies) you, normally do business with. The email, for example, might tell, you that some sort of service normally provided to you is due, to expire soon. The email directs you to a phony Web site made, to look like the site of the company you do business with. Once, there, you are asked to provide personal information such as credit card details or social, security number so that your service which was hatted, can be continued., , Keylogger, , Similar to a part of spyware, a keylogger (short for, keystroke logger) is a software or technology that, tracks or logs the keys struck on your keyboard, typically, in a covert manner so that you don’t know that your, actions are being monitored. This is usually done with, malicious intent to collect your account information,, credit card numbers, user names, passwords and other, private data., , Trojan, , Trojans leave your computer completely unprotected, which can, mean that hackers can steal any data from your system. Trojans often, present themselves as harmless computer programs so that hackers, can penetrate your computer without being detected., , Rogue Security Software, , Leveraging the fear of computer viruses, scammers have, found a new way to commit Internet fraud. Rogue security, software is malicious software that misleads users to believe, there is a computer virus installed on their computer or, that their security measures are not up to date. Then they, offer to install or update users’ security settings. They’ll, either ask you to download their program to remove the, alleged viruses or to pay for a tool. Both cases lead to, actual malware being installed on your computer., Cyber Security and Netiquette 151
Page 5 :
Ransomware, , Ransomware is a type of malware that restricts access to your computer, or your files and displays a message that demands payment for the, restriction to be removed. When the payment is made, the criminal, provides a decryption key that will give the victim access to their, systems again., , DDoS Attacks, , In a DDoS (distributed denial-of-service) attack, crooks overload an organization’s servers, in order to make its website temporarily unavailable. This can serve one of two purposes., It could be an act of revenge against an organization, or a distraction that allows the crooks, to break into the organization while its staff are focusing on restoring its website., , Overseas Money Transfer Scam, , If an email sounds too good to be true, then it, is. You'll receive an email from someone claiming, to represent a foreign government or someone, formerly involved with a foreign government., The person will claim that, through a change in, leadership or death, he or she has been left with, a large amount of money. They will ask your help, getting the money out of the country and if you, help you can receive a large share of the money. The message will go on to ask you to, respond to the email with bank account information and other personal information., , Info, New Term:, Cybercrime is defined as a crime in which a computer or computer technology is used as the object of, the crime (hacking, phishing, spamming) or is used as a tool to commit an offense., , Cyber Safety Measures, Install Anti-Virus Software, , Antivirus software is the ‘policeman’ at the gate of the computer, system. It protects the computer from incoming threats and, seeks out, destroys and warns of possible threats to the system., It provides two-way protection which puts a check in every, incoming and outgoing data/mail through the Internet and blocks, the same if it finds something suspicious during transmission., 152 Brainy Gigabyte+ 7
Page 6 :
New viruses are coming out all the time. It is the job of the antivirus software to keep up, with the latest threats. This is achieved by daily updates of the antivirus database definitions,, which counteract the latest threats to provide constant protection., , Update Your Operating System & Software, , Keep your computer up to date. Check from time to time if there are updates on the operating, system and software available. The updates will help fix certain irregularities in your system, that may decrease the risk of threats entering your computer., , Set Up Firewalls, , Firewalls are effective gatekeepers between your, computer and the internet and one of the major barriers, to prevent cyber threats such as viruses and malware., A firewall is an application that protects your computer, from the hackers gaining unauthorized access to your, computer. Setting up a personal firewall will dramatically, reduce the possibility of your computer being attacked, by Internet threats. Software firewalls often come as part of an operating system. For, example, Windows include Windows Firewall and you should always turn it on., , Avoid Public Wi-Fi, , Do not easily trust public Wi-Fi. Anyone malicious in your, surroundings may be secretly accessing your accounts or stealing, your passwords through the Wi-Fi. It is recommended that you, use a Virtual Private Network or VPN that encrypts your, connection by connecting to a safe and secure server in the middle., , Use Strong Passwords, , A strong password is the equivalent of a deadbolt on a door. The, more difficult it is to gain entrance to your accounts, the safer your, accounts are. Make your passwords difficult to figure out, by using, a combination of letters, numbers and special characters and most, importantly, change them regularly., Make it difficult for a thief to discover your password by being creative., • Figure out something you will easily remember but that doesn't contain obvious words, or dates, such as family or pet names and birthdays or addresses., • Make sure it has at least eight characters or longer and uses a combination of upper, and lowercase letters, numbers and special characters (for example, abs%12DE)., Cyber Security and Netiquette 153
Page 7 :
Using Secure Internet Browser, , First things first, we recommend using a reputable Internet browser to ensure the basic, security, like Google Chrome, Microsoft Edge, Mozilla FireFox, Apple Safari etc. These, browsers can protect you from most phishing of contents and malware., , To keep safe online, you should also make sure the site you’re going to visit is secure. Go, to the HTTPS pages instead of HTTP pages. HTTPS, is the secure version of HTTP and the, S at the end means secure. All your communications between your browser and the website, are encrypted on HTTPS pages., , Make Backups, , Backups may not sound like a way to keep your computer, safe, but if something damages the computer or you have, a security problem, you can quickly recover if you have, a recent backup of all your data. Hard drives crashes,, computers are stolen, accounts are hacked but if you have, a backup, you can at least get all of your data back., There are many ways to perform a backup, such as both by hardware (USB drives and external, hard drives) and using software (archiving and cloud). Keep backed up data in a secure location., , Download From Trusted Websites, , Just like suspicious emails, unknown websites and downloads may contain potential risks, that do harm to your devices or data. Along with the possibility of significant legal penalties,, downloading music and movies from illegal websites can be harmful to your machine. These, downloaded files are sometimes riddled with viruses and spyware., , Understanding Netiquette, What makes ‘human beings different from animals’? The answer is very simple because, human beings knows how to carry themselves in the society. In every place of our society,, there are etiquette to be followed. Be it a restaurant, school,, office or restroom, every place has its own set of rules., Similarly, internet also has etiquette which must be followed, by a person while using the network. However, there is a, difference between ethics in the real world and ethics in the, Internet world called as Netiquette., 154 Brainy Gigabyte+ 7
Page 8 :
It is a combination of the words network and etiquette, is the basic etiquette to be followed, on the internet. It is the unofficial set of rules, which is expected to be followed by every, cyber-citizen. This simply means the use of good manners in online communication such as, e-mail, forums, blogs and social networking sites., , Definition, ‘Netiquette’ refers to Internet etiquette means the use of good manners in online communication such, as e-mail, forums, blogs and social networking sites., , Why do we need Netiquette?, • It is important to use netiquette because communication online is non-verbal. This, type of communication does not allow the person to see facial expressions, body, language or hear intonation. Because of this, messages can often be misinterpreted., By following netiquette, online communication becomes clearer and meaningful., • We need Netiquette because this will be our guide while using Internet facilities such, as individual Web sites, emails, newsgroups, message boards, chat rooms or Web, communities., • We must also follow this for us to be disciplined and for us to be a better person., When we follow netiquette, we respect other people., , Principles of Proper Netiquette, Netiquette are not rigid rules that people have to follow. They are general guidelines which,, when followed optimally, make the internet a well-organized and civic forum. These rules, make the internet conversations unambiguous and help protect you from the unsafe world, of the cyber. The way you talk on internet shows your fluency and your command over your, language, so make sure you do not underestimate grammar on this forum., , Be Respectful, , Everyone has different feelings and opinions and, it is important to respect this online. You may wish, to comment on something someone has shared, but always remember that behind every account is, a real person. If you wouldn’t say it to someone’s, face, the internet is not the place to say it either., , Follow the Rules, , If a website, discussion group or mailing list has posting guidelines in place, follow them., Failure to do so often irritates the administrators and could get you out of the group or off, the website., Cyber Security and Netiquette 155
Page 9 :
Help the Newbies, , In cyber world, newbies is the term used for who is new to the online, communication or to the Internet. A good netiquette dictates that, you share your knowledge to new users by answering some of their, questions. Remember, you too were a newbie once., , Respect People's Privacy, , Don't forward information sent to you without checking with the original sender first. Use, BCC (blind carbon copy) rather than CC (carbon copy) if you are sending something out, to more than one person. You might think that we are all friends online, but your friends may, not want their names and or email addresses publicized to your acquaintances that they do, not even know., , Use Mixed-Case Letters, , Using all capital letters is considered SHOUTING, and is in bad taste. Using all lower-case, letters can make your message difficult to read. Make sure that you turn off your caps lock, before you start typing an email message or discussion group posting or any other form of, online communication., , Do Not Reply to Strangers, , If you receive e-mails from people you don’t know then do not reply. It is not safe. The worst, can happen, if someone purposely wants to hurt you or your system. If you find an e-mail, offensive or insulting do not reply. Ignore such offensive mails and block the sender for, good. If still the mails get through and the content crosses all limits, then save the email and, report it to the administrators and the customer service., , Use Emoticons, , Since the conversation is not face-to-face, it gets difficult to, understand whether a said comment was serious, rude or humorous., Emoticons or the smileys come as great help in this case. The smileys, show if what you are saying is serious or funny or the like. It not only, helps to clear understanding but also adds color to the message., , Your Digital Footprint Matters, , Your digital footprint is all the stuff you leave behind as you use the, Internet. Comments on social media, Skype calls, app use and email, records, it’s part of your online history and can potentially be seen by, other people or tracked in a database. The digital footprints we leave, do have an impact on our lives and so it is important to understand, how to manage it. Always be a decent and responsible netizen., 156 Brainy Gigabyte+ 7
Page 10 :
Info, New Term:, Netizen is the term used to describes a person actively involved in online communities or the Internet, in general., , Do not Re-Distribute Material that is Not Yours, , This is essentially copyright infringement. Taking images from another website for redistribution, forwarding a personal email message or sharing files or phrases that do not, belong to you is considered to be rude and in many cases illegal., , Think Before you Hit the ‘Send’ Button, , Think before you send your message. Once you click on the send, option, you cannot take anything back. Hence, know what you are, typing and be polite with your words., , Now You Know, • Cyber security refers to a set of techniques used to protect the integrity of networks, programs, and data from attack, damage or unauthorized access., • ‘Malware’ is short for ‘malicious software’, that are computer programs designed to infiltrate, and damage computers without the users consent., • A cyber attack is a strike against a computer system, network, or internet-enabled application, or device., • Hacking is the process of gaining unauthorized access into the computer system or group of, computer systems or website or social media site or an email account., • A computer virus is a malicious software program loaded onto the user’s computer without, his/her knowledge and performs malicious actions., • Phishing is a cybercrime and a method of trying to gather personal information using, deceptive e-mails and websites., • Adware is a type of malware software that is designed to track data of browsing habits., • Spyware is a type of malware that collects and shares information about a computer or, network without the user’s consent., • Keylogger is a software or technology that tracks or logs the keys struck on keyboard without, user’s knowledge or permission., • Antivirus software is a program or set of programs that are designed to prevent, search for,, detect, and remove computer viruses and other malicious software., Cyber Security and Netiquette 157
Page 11 :
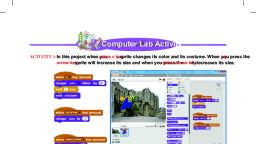
• Netiquette’ refers to Internet etiquette means the use of good manners in online, communication such as e-mail, forums, blogs and social networking sites., • A digital footprint is a trail of data that user creates while using the Internet. It includes the, websites they visit, emails they send and information they submit to online services., , Computer Lab Activity, ACTIVITY 1: �Knowing about Anti-Virus, • W, � ith the help of Internet, find out the names of some latest computer viruses and anti virus, programs., • In the school computer lab see how anti virus works., • Learn how to update the anti virus programs., • Learn how to scan a folder on hard disk / pen drive., ACTIVITY 2: �Turn Computer's Firewall On and Off., A firewall is a layer of security which designates what information traffic is and isn't allowed, to enter your computer on a network. Generally, they let good traffic through, while keeping, hackers, malware and other unsavory traffic out., Step 1: �Click on the Start menu and type windows firewall in the search box., Step 2: P, � ick the ‘Windows, Firewall’ option that, pops up in the search, results., Step 3: I� n the left sidebar, click, 'Turn Windows Firewall, On or Off '., Step 4: U, � nder 'Private Network, Settings', click 'Turn Off, Windows Firewall'. If, you want to turn it back, on, just click the 'Turn, on Windows Firewall', button above it., If you have another firewall as part of your anti-virus software, keep the Windows Firewall, On for public networks. You'll need it as extra protection when you're on an insecure Wi-Fi, network, like a coffee shop, since you don't know who else is connected., 158 Brainy Gigabyte+ 7
Page 12 :
Assessment Sheet, A., , Tick () the correct option for the following statements., 1. T, � he term that refers to the security precautionary steps taken to protect computing resources against, cybercrime., , a), , b), , E-Security, , Computer Security, , c), , Cyber Security, , 2. A crime in which a computer or computer technology is used as the object of the crime., a), , b), , Computer Crime, , Cyber Crime, , c), , Electronic Crime, , 3. Cyber crime is crime that involves:, a), , Computer, , b), , c), , Internet, , Smartphone, , d), , Any of them, , 4. It is the process of gaining unauthorized access into a computer system or a website., a), , b), , Hacking, , c), , Checking, , Cracking, , 5. Computer viruses are designed for one of the following., a), , Steal Data, , b), , Corrupt Data, , c), , Delete Data, , d), , All of them, , 6. �A software utility designed to protect your computer against computer viruses., a), , Disk Cleanup, , b), , System Restore, , c), , Anti-Virus, , b), , Antivirus, , c), , Spyware, , 7. Key logger is a:, a), , Firmware, , 8. A, � type of malware software designed to track data of user’s browsing habits and based on that, show, advertisements., a), , Spyware, , b), , Keylogger, , c), , Adware, , 9. The term used to describe the etiquette to be followed on the internet., a), , Cyber Etiquette, , b), , NetEtiquette, , c), , Netiquette, , 10. One of the following is not a principal of netiquette., a), , Respect People's Privacy, , b), , Follow the rules of the website, , c), , Use mixed case letters in messaging, , d), , Always reply to strangers, , Cyber Security and Netiquette 159
Page 13 :
B., , Tick () the correct and cross () the wrong ones in the following statements., 1. Cybercrime is a legal activity done through computer with Internet connection., 2. Computer virus is a kind of program that disrupts the normal functioning of a computer., 3. To protect data and important information, passwords should not be changed., 4. I� t is OK to give your credit card information in an e-mail if the store you were shopping, online asks for it., 5. Using phone number as a password is always recommended as a secured password., 6. In E-mail, using all capital letters is considered as shouting., , C., , Read the following statements to name the correct term., Help Box, , D., , Firewalls, Digital Foot print, Password, Newbies, , 1. Someone who is new to the online communication or to the Internet., , ____________________, , 2. The stuff you leave behind as you use the Internet., , ____________________, , 3. The gatekeepers between your computer and the internet, , ____________________, , 4. This is the key for user's online account., , ____________________, , Read the following sentences and name the type of cybercrimes/cyber-attacks., 1. A, � scam where an official-looking email is sent to an unsuspecting user, that tricks out their username, password or other information., , ____________________, , 2. A scam where someone encrypts your data and then the sender demands, money to free your data., ____________________, 3. M, � alicious software that presents itself as harmless computer program, so that hackers can steal any data from your system., , ____________________, , 4. A, � n attack, overloading an organization’s servers in order to make its website, or network temporarily unavailable., ____________________, 5. M, � alicious software that misleads users to believe there is a computer virus, installed on their computer or that their security measures are not up, to date., ____________________, E., , Explain the following terms:, 1. Cyber Crime, , _________________________________________________________________, , 2. Computer Virus _________________________________________________________________, 3. Hacking, , _________________________________________________________________, , 4. Keylogger, , _________________________________________________________________, , 160 Brainy Gigabyte+ 7
Page 14 :
5. Phishing, , _________________________________________________________________, , 6. Digital Footprint _________________________________________________________________, F. �Answer the following questions., 1. What is Cyber Security and its importance?, _______________________________________________________________________________, _______________________________________________________________________________, 2. Differentiate between Adware and Malware., _______________________________________________________________________________, _______________________________________________________________________________, 3. Why anti-virus software is called as the policeman at the gate of the computer system?, _______________________________________________________________________________, _______________________________________________________________________________, 4. What do you understand by the term ‘Netiquette’ and why is it important?, _______________________________________________________________________________, _______________________________________________________________________________, 5. List some proper principles of Netiquette to be followed by citizen of the net., _______________________________________________________________________________, _______________________________________________________________________________, , Application Based Questions, 1, , � arun is Internet savvy, he spends lot of time with Internet for his study purpose and for, V, entertainment. Help him to select the correct answer in the following situations., a) When he post something on the Internet, how long does it stay there?, , , , 1 Week, , Forever, , , , 2 Year, , Until he deletes, , b) H, � e is about to join an amazing new website that his friends are all a part of. What information is OK, to give online?, , , Parent’s Credit Card Number, , Phone Number, , , , Address, , Nick Name, , c) H, � e is having trouble doing an activity on a safe site he uses at school. His friend offers to help but, needs his password. Should he give the password to his friend?, , , Yes, , It depends, , Strictly No, Cyber Security and Netiquette 161
Page 15 :
d) �He is on the computer when suddenly an advertisement for ‘Free Ring Tones’ pops up! Cool!!! All, he has to do is enter his parent’s credit card number, but it won’t cost anything. What should he do, and why?, � , , , , If it look like a sage email, click on it and then ask parents for the information., , , , Click on it. If it is free, what’s the harm?, , , , Ignore it, this is a spam message that could steal money from parent’s bank account., , e) �He just got a new WhatsApp message on his laptop. It is not in his contact list, but he think he might, know the person. How do he respond?, , , Save the message and tell parents, , , , Delete the message, , , , Reply to message, it’s okay to talk to strangers, , , , Reply to message asking who the person is, , 2, , � adhika is new to cyber world, as she recently started browsing the Internet. Mention some, R, precautions she should keep in her mind at the time of browsing., ________________________________________________, ________________________________________________, ________________________________________________, ________________________________________________, ________________________________________________, , 3 �, Supriya is planning to buy shoes from the shopping sites using Internet. Suggest her what she should, check in the address bar of the web browser after opening the site of the seller., _________________________________________________________________________________, _________________________________________________________________________________, 4, , � haru’s computer got infected with a virus, which led to slower processing speed of the system. Which, C, software should she buy in order to solve this problem?, _________________________________________________________________________________, , 162 Brainy Gigabyte+ 7
Page 16 :
National Cyber Olympiad, Practice Test Paper, Choose the correct answer out of the four options given below in each question. Mark your choice, in the answer sheet given at the end of this test paper., , Computer and Information Technology, 1. �Which of the following options will complete, the given series?, , ?, a), , b), , c), , d), , 2. �If TOGETHER is written as RQEGRJCT, then, how will PAROLE be written?, a) NCPQJG, b) NCQPJG, c) RCPQJK, d) RCTQNG, 3. �In the given figure, the triangle represents girls,, square represents sportspersons and circle, represents coaches. Which portion of the figure, represents girls who are sportspersons but not, coaches?, a) P, U, Q, b) Q, P, R, c) R, T, S, d) S, 4. �Five boys A, B, C, D and E are standing in a row., A is between C and D and B is between D and, E. Which of the following pairs represents the, boys standing at both the ends?, a) C, B, b) E, C, c) E, A, d) A, C, 5. �A man goes towards East five kilometres, then, he takes a turn towards right and goes five, kilometres. He again takes a turn towards right, and goes five kilometres. With respect to the, point from where he started, where is he now?, a) East, b) North, c) West, d) South, , 6. �MBP is a short form for a famous high end, notebook from Apple. It is called _________., a) Macintosh Book Pro, b) Mac Book Programmable, c) Mountain Book Pro, d) MacBook Pro, 7. �You can join an Active Directory domain in, which of the following Windows 7 versions?, i) Windows Home Edition, ii) Windows Professional Edition, iii) Windows Ultimate Edition, iv) Windows Enterprise Edition, a) Only (i) and (ii), b) Only (iv), c) Only (ii), (iii) and (iv) d) All of these, 8. �The function of ‘Wrap Text’ icon in MS Excel is, used to ______., a) Join selected cells into one larger cell, b) Rotate text to a diagonal angle, c) �, Make all content visible within a cell by, displaying it on multiple lines, d) Highlight interesting cells, 9. �Match the following terms with what they stand, for., Term , Stands for, i) .com, (A) Education, ii) .edu, (B) India, iii) .in, (C) Australia, iv) .au, (D) Commerce, a) (i)-(A), (ii)-(B), (iii)-(C), (iv)-(D), b) (i)-(B), (ii)-(C), (iii)-(D), (iv)-(A), c) (i)-(C), (ii)-(D), (iii)-(A), (iv)-(B), d) (i)-(D), (ii)-(A), (iii)-(B), (iv)-(C), National Cyber Olympiad 163
Page 17 :
10. �, A browser is an interactive program that, permits a user to view web pages on the, computer. The browser performs which of the, following services?, a) �Connecting to the source computer whose, address is specified, b) Requesting new page from the server, c) Receiving new page, d) All of these, 11. �, Modern Computers compared to earlier, computers are _______., a) Faster and larger, b) Less reliable, c) Larger and stronger d) Faster and smaller, 12. �In MS-Word, which shortcut key is used to, increase the font size of text?, a) Ctrl + F, b) Ctrl + Alt + F, c) Ctrl + Shift + >, d) Ctrl + Shift + X, 13. �, Match the virus types given in Column-I, with their corresponding examples given in, Column-II., Column-I, Column-II, A) Macro Virus, i) Lamer, Exterminator, B) Boot Sector Virus, ii) Natas, C) Polymorphic Virus iii) Melissa, a) (A)-(iii), (B)-(i), (C)-(ii), b) (A)-(i), (B)-(ii), (C)-(iii), c) (A)-(ii), (B)-(i), (C)-(iii), d) (A)-(iii), (B)-(ii), (C)-(i), , 14. �Match the following output devices given in, Column-I with their descriptions given in, Column-II., Column-I, Column-II, A) Voice, i) It produces audio, Response output by selecting, System an audio output, from a set of pre recorded audio, response., B) Voice, ii) It enables a, Reproduction computer to talk, System to a user., c) Speech, iii) It converts text, Synthesizer information into, spoken sentences., a) (A)-(ii), (B)-(i), (C)-(iii), b) (A)-(i), (B)-(ii), (C)-(iii), c) (A)-(iii), (B)-(ii), (C)-(i), d) (A)-(i), (B)-(iii), (C)-(ii), 15. �Which of the following QBASIC codes will, produce the given output?, Output: 1 2 3, a) FOR x = 1 TO 3 b) FOR x = 1 TO 5, PRINT x; PRINT x, NEXT x NEXT x, c) FOR x = 1 TO 3, d) FOR x = 1 TO 3, PRINT x PRINT x, EXIT FOR EXIT FOR, NEXT x MORE x, , Answer Sheet, , Darken your choice with HB pencil, 1., , A, , B, , C, , D, , 6., , A, , B, , C, , D, , 11., , A, , B, , C, , D, , 2., , A, , B, , C, , D, , 7., , A, , B, , C, , D, , 12., , A, , B, , C, , D, , 3., , A, , B, , C, , D, , 8., , A, , B, , C, , D, , 13., , A, , B, , C, , D, , 4., , A, , B, , C, , D, , 9., , A, , B, , C, , D, , 14., , A, , B, , C, , D, , 5., , A, , B, , C, , D, , 10., , A, , B, , C, , D, , 15., , A, , B, , C, , D, , 164 Brainy Gigabyte+ 7