Page 1 :
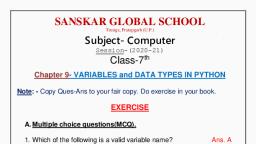
Sanskar Global School,Pratapgarh, Chapter 12- CYBER CRIME, Class-6th, Subject-Computer, Session 2020-21, Note: Copy it to your fair copy., E. Short Answer Type Questions:, Q1. What is a cybercrime?, Ans1. Cybercrime is defined as a crime in which a computer is the object of the crime or, is used as a tool to commit a crime. Example: Hacking, Phishing., Q2. What is hacking?, Ans2. Hacking refers to unauthorized intrusion into a computer system or a network. The, person engaged in hacking activities is known as a hacker., Q3. What do you understand by term Phishing?, Ans3. Phishing is a cybercrime in which the personal information of the target is, obtained by someone posing as a legitimate user., , F. Long Answer Type Questions:Q1. What is a computer virus? Name its types., Ans1. A computer virus is a type of a malware program, which gets replicated by, inserting the copies of itself into the other computer programs or the data files of the, hard drive. It disrupts the normal functioning of the computer., Types of computer viruses: Boot Sector, Program File, Memory Resident, Overwrite, and Multipartite Virus., Q2. Write the difference between Ethical Hacker and Cracker., Ans2. Ethical Hacker: A hacker who gains an authorized access to systems with a view, to identify and fix the weaknesses. They are appointed by software companies., Cracker: A hacker who gains unauthorized access to the computer systems for, personal gain. Their intent is to find banks or other companies with weak security and, steal money or credit card information. They are also known as crackers. Their actions, are malicious.
Page 2 :
Q3. How is Boot Sector Virus different from Program File Virus?, Ans3. Boot Sector Virus: This virus affects the boot sector of floppy or hard disk where, start-up files are found. The viruses run at bootup, allowing them to execute malicious, code during start-up time. They are difficult to remove, requiring a full system format., Examples are: Disk killer, Stone virus., Program File Virus: This type of virus infects program files, such as applications,, games or executable files (files with .EXE or .COM extension). When one of these, programs are run then directly or indirectly the virus is activated, producing the, damaging effects, it is programmed to carry out. Examples are: Sunday, Cascade, etc., G. Application Based Questions:Q1. Shrey’s computer is not working properly. The executable files and programs with, extension like .exe, .com, etc. on his PC have got infected. Which type of virus has, entered into his computer?, Ans1. Program File Sector, Q2. Divya has received an Email from an unknown source claiming that it is a legitimate, institution. The sender demands the bank account details and credit card details. What, kind of Cybercrime could it be?, Ans2. Phishing, , EXERCISE, A. Tick () the correct answer., 1. The virus can not affect the following parts of computer system., a) RAM, b) Mouse, c) Hard disk, Ans. (b), 2. VIRUS stands for, a) Very Intelligent Resource Under Security, b) Vital Information Resource Under Seize, c) Viral Important Record User Search, Ans. (b), 3. Which among the following virus is a combination of Boot Sector and Program, File virus?, a) Boot Sector, b) Multipartite Virus c) Polymorphic Virus, Ans. (b), 4. ______________ is referred to the code of behaviour to be followed when, online., a) Cyber Laws b) Cyber Crime, c) Cyber Ethics, Ans. (c), 5. A ____________ virus is associated with application software like Word, Excel, and PowerPoint., a) Program File, b) Macro Virus, c) Boot Sector, Ans. (a)
Page 3 :
B. Fill in the blanks., 1. Hacking refers to unauthorized intrusion into a computer system., 2. A computer virus is a type of malware which gets replicated and disrupts, the normal functioning of the computer., 3. A cracker gains unauthorized access to the computer system for personal gain., 4. A stalker can be online stranger or a person known to the targeted person., 5. Boot Sector virus affects the boot sector of floppy or hard disk., , C. Write True (T) or False (F)., 1. Identity Theft refers to the act of stealing or misusing someone’s personal, information., Ans. (T), 2. Cybercrime is an illegal activity done through the Internet. Ans. (T), 3. Worms damage the boot sector of the hard disk., Ans. (F), 4. An ethical hacker gains an unauthorized access to the system for personal gain., Ans. (F), 5. A file with extension .exe can be a memory resident virus., Ans. (F), D. Read the following sentences and name the type of cybercrimes., 1. To steal someone’s personal information to gain access to personal details like, name, address, date of birth, bank accounts, etc. Identity Theft, 2. An act of threatening or harassing someone by finding out information about, them. Cyber Security, 3. A type of attack where the attackers attempt to prevent legitimate users from, accessing the service. Denial of Service, 4. Unauthorized intrusion into a computer system or network. Hacking, 5. Using Internet to cause large scale disruption of telecommunication network,, attacks on important institutions. Cyber Terrorism
Page 4 :
SANSKAR GLOBAL SCHOOL, Teunga, Pratapgarh (U.P.), , Home - Assignment, , Class-VIth, Chapter-12- CYBER CRIME, Note:- Read the instructions carefully:a) Read the Chapter., b) Answer the following Questions and copy this Home-Assignment, in your Computer fair copy., c) Learn it by heart, it will be asked., Q1. What is the full form of VIRUS?, Q2. Distinguish between Cyber Ethics and Cyber Laws., Q3. Define Denial-of-Service (DoS) briefly., Q4. Give two examples of Worm., Q5. Write True (T) or False (F):a) Trojan Horse does not replicate or spread like a virus., b) Gray Hat is a hacker who is in between Ethical hacker and Cracker., , ****